|
Secretaris-Generaal VN
Geregistreerd: 9 december 2010
Berichten: 36.784
|
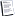
U.S. military hackers have been given the go-ahead to gain access to Russian cyber systems if meddling in America’s 2018 elections is confirmed.
The U.S. intelligence community and the Pentagon have quietly agreed on the outlines of an offensive cyberattack that the United States would unleash if Russia electronically interferes with the 2018 midterm elections on Nov. 6, according to current and former senior U.S. officials who are familiar with the plan.
In preparation for its potential use, U.S. military hackers have been given the go-ahead to gain access to Russian cyber systems that they feel is needed to let the plan unfold quickly, the officials said.
The effort constitutes one of the first major cyber battle plans organized under a new government policy enabling potential offensive operations to proceed more quickly once the parameters have been worked out in advance and agreed among key agencies.
...
NSPM 13, which remains classified, was the backbone of Trump’s new National Cyber Strategy, a mostly unclassified public document that was released in September.
That strategy was rolled out with descriptions from national security adviser John Bolton of a more aggressive use of cyber weapons, consistent with his general foreign policy stance since taking the job in April. At that time, officials declined to provide any specifics on how the new policy would make cyber response faster, or cut down on red tape, but claimed it would do both.
During a press conference on Sept. 20 to roll out the new cyber strategy, Bolton said that “for any nation that’s taking cyber activity against the United States, they should expect, and this is part of creating structures of deterrence, so that it’s publicly known as well, we will respond offensively as well as defensively.” During a speech on Oct. 31, he said the United States was “right now undertaking offensive cyber operations” to safeguard the election, without detailing what those are.
According to sources, the new executive order, NSPM 13, is designed around the idea of pre-approved “Concepts of Operations” — one of the first of which is the plan to act against Russia if key red lines are crossed. The concepts set the types of targets and the boundaries for types of action through coordination between agencies.
It doesn’t require a full meeting of Cabinet officials and can exclude some of the decision makers who were part of the PPD 20 process. Most of the coordination will take place between the Office of the Director of National Intelligence, the Pentagon, and the Department of Homeland Security, according to sources.
“The concept is that you would approve a category of activities against a defined adversary, that would be pre-approved by the appropriate people, within some left-and-right bounds,” one of the officials said. Once a concept is approved, an agency can scout a target and gain access, and sometimes might go ahead and take action with limited notice to other coordinating agencies.
...
The military and intelligence agencies then deploy those vulnerabilities whenever they need to break into systems. The public got a hint of the types of inroads government hackers can make when some pathways stockpiled by the National Security Agency were collected by a group calling itself the Shadow Brokers, which released them publicly beginning in 2016. One of those vulnerabilities served as the backbone of the WannaCry attack, which the Trump administration publicly blamed on North Korean hackers, and which eventually spread to 300,000 computers in 150 countries in 2017.
U.S. officials have never publicly claimed responsibility for the use of cyber weapons, although reports have tied U.S. government hackers to disruption of North Korea and Iran’s nuclear programs.
...
Its general outlines were disclosed in late 2017, when public documents stated that government hackers tell software makers about roughly 90 percent of the vulnerabilities they find while testing nearly every widely used piece of software. A former official familiar with the program confirmed that figure, noting that there is some monthly fluctuation, and saying that many of the public security fixes included in operating system updates are actually first uncovered by government hackers.
“The 10 percent we keep is for our national security purposes,” a former White House official said. “We keep them for a reason.”
The Pentagon (mol Bolton) has prepared a cyberattack against Russia
https://ca.news.yahoo.com/pentagon-p...170856445.html
Meer:
 John Bolton, who will become President Trump’s national security advisor on April 9, is eager to start a cyber war with Russia and North Korea. Bolton’s point of reference is the Sony Pictures hack in 2014. It was reported the Sony attack was in response to the release of the satire film The Interview which portrays the assassination of North Korean leader Kim Jong-un by the CIA. Although the establishment media dutifully reported North Korea was the culprit, computer security experts believe it’s unlikely they’re responsible. Experts believe the likely perpetrators were disgruntled insiders or hacktivists. None of this matters if your intention is to build a narrative that North Korea, China, and Russia are engaged in nefarious plots to disrupt American computer networks, including networks connected to financial institutions and even the US power grid.
John Bolton, who will become President Trump’s national security advisor on April 9, is eager to start a cyber war with Russia and North Korea. Bolton’s point of reference is the Sony Pictures hack in 2014. It was reported the Sony attack was in response to the release of the satire film The Interview which portrays the assassination of North Korean leader Kim Jong-un by the CIA. Although the establishment media dutifully reported North Korea was the culprit, computer security experts believe it’s unlikely they’re responsible. Experts believe the likely perpetrators were disgruntled insiders or hacktivists. None of this matters if your intention is to build a narrative that North Korea, China, and Russia are engaged in nefarious plots to disrupt American computer networks, including networks connected to financial institutions and even the US power grid.
__________________
Citaat:
Oorspronkelijk geplaatst door Salah
Het zal weer het gekende Zonbron momentje zijn.
|
 HIER HIER
|